Poor Dumb Networkers Teach Smart Programmers Awareness

Have you heard of the OSI Model? And can you differ what each layer do besides of the obvious? This is an article about the model, the layers and the shark.
The Model
OSI Model was created to standardize network communication protocols, and use layers to divide different levels of abstraction. The principles used to that were:
- A layer should be created where a different level of abstraction is needed.
- Each layer should perform a well-defined function.
- The function of each layer should be chosen with an eye toward defining internationally standardized protocols.
- The layer boundaries should be chosen to minimize the information flow across the interfaces.
- The number of layers should be large enough that distinct functions need not be thrown together in the same layer out of necessary, and small enough that the architecture does not become unwieldy.
The layered approach offers several advantages. By separating networking functions into logical smaller pieces, network problems can more easily be solved through a divide-and-conquer methodology. OSI layers also allow extensibility. New protocols and other network services are generally easier to add to a layered architecture.
The Layers
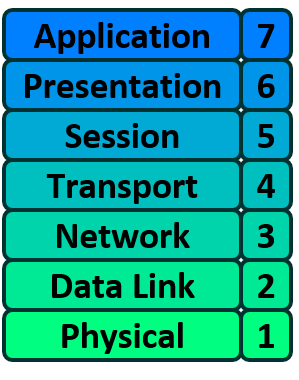
The seven OSI layers from bottom to top are:
- Physical: Connects the entity to the transmission media
- Data Link: Provides error control
- Network: Routes the information in the network
- Transport: Provides end to end communication control
- Session: Handles problems which are not communication issues
- Presentation: Converts the information
- Application: Provides different services to the application
But this article isn’t about memorizing textbook definitions. It’s about understanding — something I struggled with until I met the shark.
The Shark
Enter Wireshark, a packet analyzer that helped me see what each OSI layer really does.
When analyzing traffic, I noticed Wireshark breaks packets into sections that roughly correspond to OSI layers. Let’s walk through an example.
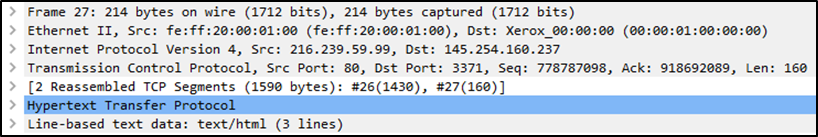
We can see seven distinct layers to the packet: frame/packet, source MAC, source IP, protocol, protocol errors, application protocol, and application data. Below we will go over the layers in more detail.
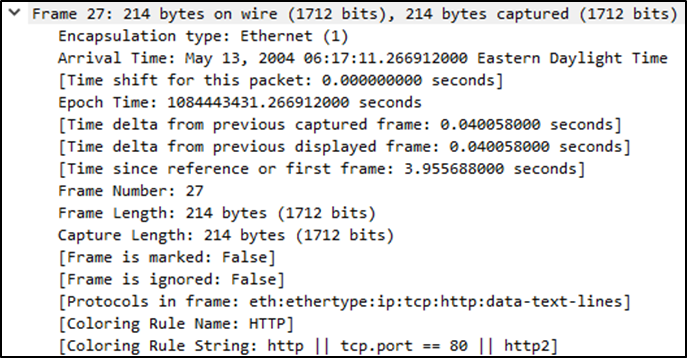
Layer 1: The Frame (Physical Layer)
This is where Wireshark shows frame-specific metadata, like the packet number and capture timestamp. It doesn’t show voltages or light pulses, but it gives insight into how the packet was physically transmitted.
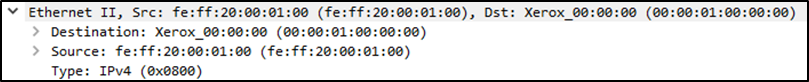
Layer 2: Source MAC (Data Link Layer)
Shows MAC addresses and Ethernet details. This is the “local” addressing used in LAN communication.
Layer 3: Source IP (Network Layer)
Here, you see source and destination IP addresses. This layer is responsible for logical addressing and routing across networks.

Layer 4: Protocol (Transport Layer)
This section includes the transport protocol (TCP/UDP), ports, and flags like SYN or ACK.
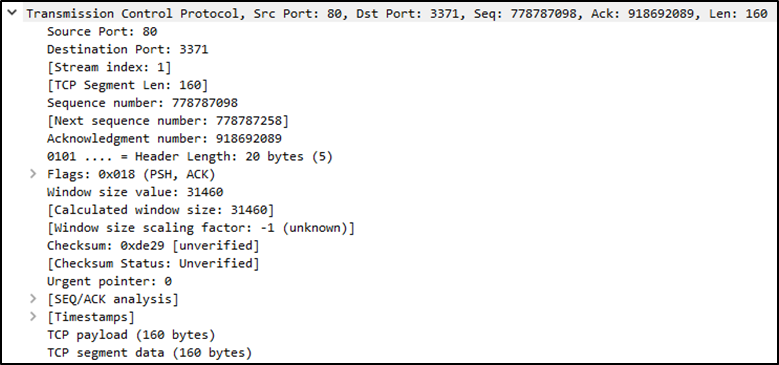
You may also spot protocol-specific details, like TCP reassembly, retransmissions, or out-of-order packets — still part of this layer.
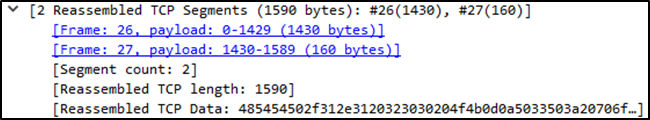
Layer 5–7: Sessions, Presentation & Application?
Here’s where things blur.
In Wireshark, Layer 5 (Session) and Layer 6 (Presentation) don’t have clear separation. That’s because modern protocols often handle session control and presentation formatting within the application-layer protocols themselves.
Instead, Wireshark groups layers 5–7 under what it calls Application Layer protocols, such as HTTP, FTP, or SMB.
Layer 7: Application Protocol
Wireshark shows you protocol-specific details — headers, commands, status codes — everything the user-level application needs.
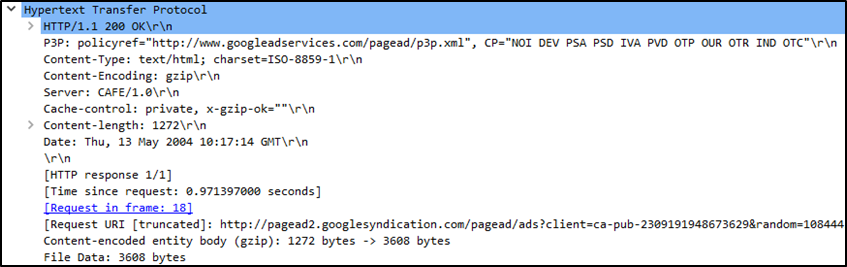
Application Data
This is the payload — raw data being transferred, like an HTML page, file content, or form data.
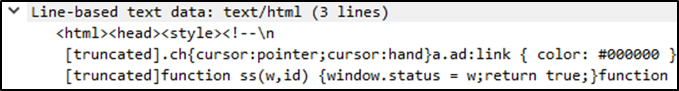
So, Where Are Layers 5 and 6?
You’re not missing them — they’re just not visibly separated in Wireshark.
- Session Layer (Layer 5) handles connections and sessions between systems, but many modern protocols (like HTTP/2) bundle session handling into the application protocol itself.
- Presentation Layer (Layer 6) takes care of formatting, encryption, and compression — again, these are usually built into the application layer (e.g., TLS for encryption, GZIP for compression).
So, while OSI offers a conceptual model, Wireshark shows a practical view — how protocols are implemented in real-world traffic, often blending layers 5–7 together.
As someone who often needs visual examples to better understand things, the shark really helped me with this one. And in case you often forget the layer names, here is something to remember:
Poor Dumb Networkers Teach Smart Programmers Awareness
